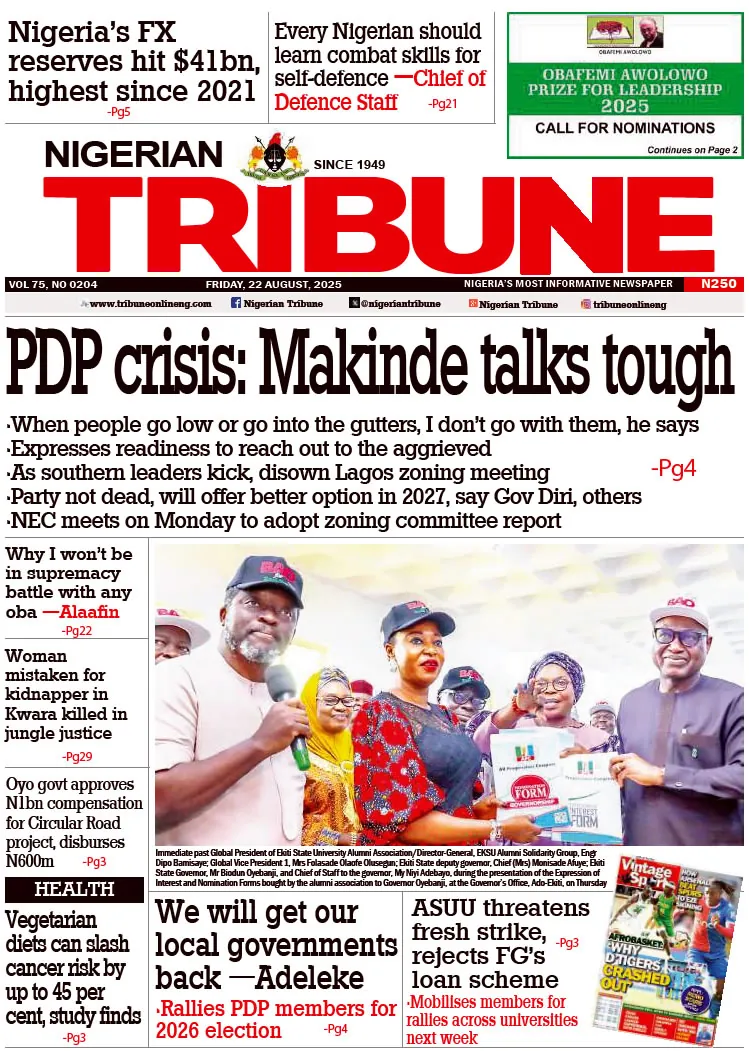
In a recent cybersecurity breakthrough, Christian Bassey, a highly skilled Nigerian threat intelligence researcher at Wazuh-the largest open source SIEM/XDR platform, unveiled an innovative method to detect Cobalt Strike beacons.
Red teams often employ Cobalt Strike beacons for adversary emulation, and malicious threat actors exploit it to infiltrate organizations. Christian said the driver behind his research on detecting beacons used by Cobalt Strike is its wide adoption by various threat actors, including APT29, APT32, and FIN6, which are known for targeting organizations in the critical infrastructure sector. Organizations like banks, energy companies, and government agencies.
Christian employed the APTSimulator toolset in this work to replicate Cobalt Strike beacon activity. Then, meticulously crafted specific detection rules to identify these beacons and their associated activity. The simulation was conducted on a Windows 10 endpoint equipped with a Wazuh agent and Sysmon, while a server running the Wazuh manager was used for analysis. During the simulation, he observed the creation of named pipes, a well-known behaviour of Cobalt Strike beacons. Named pipes facilitate interprocess communication and are utilized by Cobalt Strike to transmit and receive commands between beacons and spawned processes. This behaviour was meticulously logged and analyzed to develop precise detection rules. The detection rules were also mapped to the MITRE ATT&CK framework for improved threat detection coverage.
The detailed analysis provided underscores the critical importance of advanced detection techniques in identifying malicious activities. By configuring Sysmon to capture extensive logs and leveraging the Wazuh manager for comprehensive analysis, Christian successfully detected the presence of Cobalt Strike beacons, indicating potential red teaming or malicious activity.
This groundbreaking research not only deepens the understanding of Cobalt Strike’s methodologies but also equips organizations with practical tools to fortify their cybersecurity defences. Christian’s detection rules for the Wazuh SIEM/XDR enable continuous monitoring of suspicious activities, such as the creation of unauthorized named pipes, which are indicative of a Cobalt Strike attack.
Christian’s work exemplifies the crucial role of continuous research and innovation in the field of cybersecurity. By developing precise detection rules and enhancing threat detection frameworks, he has made a significant contribution to global cybersecurity defences. Organizations can now utilize these tools to defend against increasingly sophisticated cyber threats.
The research highlights the dynamic nature of cyber threats and the necessity for adaptive cybersecurity measures. As threat actors continue to evolve their tactics, techniques, and procedures, the cybersecurity community must remain vigilant and proactive in developing advanced detection and mitigation strategies.
This groundbreaking research on detecting Cobalt Strike beacons represents a significant advancement in the field of cybersecurity. Christian and Wazuh have demonstrated their commitment to enhancing global cybersecurity defenses and safeguarding digital assets by providing organizations with the tools to detect and respond to sophisticated cyber threats.
ALSO READ THESE TOP STORIES FROM NIGERIAN TRIBUNE
WATCH TOP VIDEOS FROM NIGERIAN TRIBUNE TV
- Let’s Talk About SELF-AWARENESS
- Is Your Confidence Mistaken for Pride? Let’s talk about it
- Is Etiquette About Perfection…Or Just Not Being Rude?
- Top Psychologist Reveal 3 Signs You’re Struggling With Imposter Syndrome
- Do You Pick Up Work-Related Calls at Midnight or Never? Let’s Talk About Boundaries