In today’s digital landscape, data integrity stands as a cornerstone for the operations of both organisations and individuals.
Ituma Johnson, a renowned expert in data security, underscores the criticality of maintaining data integrity and highlights secure methods to achieve this imperative goal.
Data integrity encompasses the accuracy, consistency, and reliability of data throughout its lifecycle, from creation to storage and transmission. In an era rampant with cybersecurity threats, protecting data integrity has emerged as a top priority to thwart unauthorised access, tampering, and corruption that could wreak havoc on businesses, governments, and individuals alike.
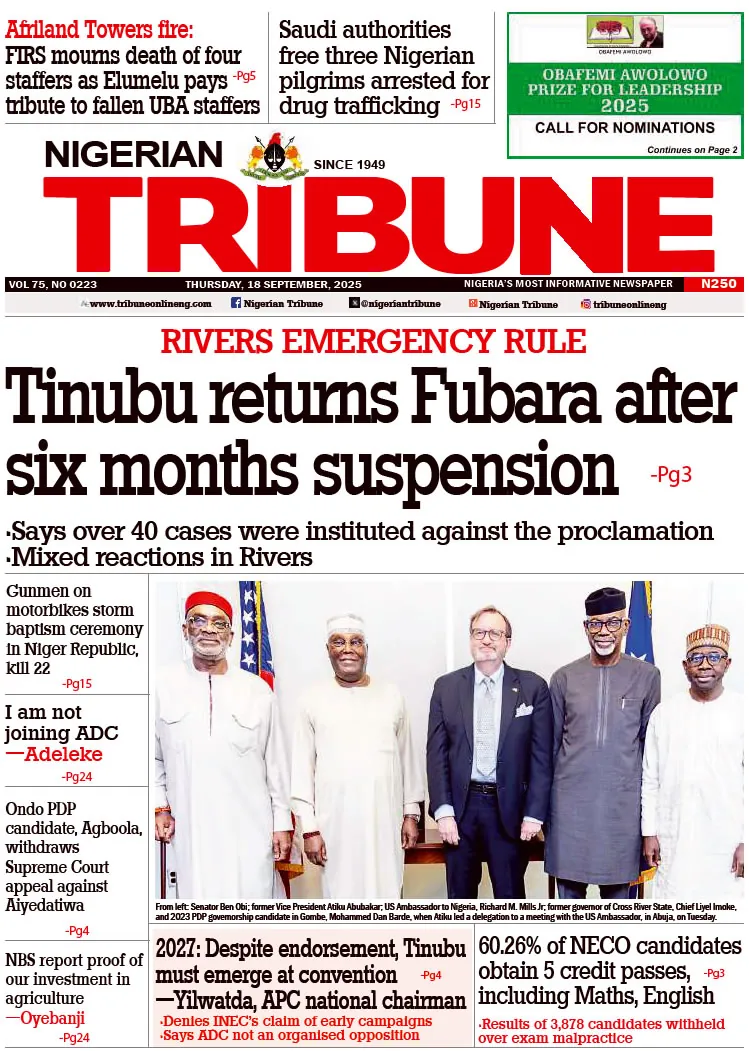
One of the primary methods advocated by Johnson is encryption. Encryption serves as a formidable barrier against unauthorised access by encoding data in a manner that only authorised parties can decipher.
By encrypting data both at rest and in transit, organisations can ensure its confidentiality and tamper-proof nature.
In addition to encryption, robust access controls and authentication mechanisms are paramount. Implementing stringent access restrictions based on user roles and privileges helps prevent unauthorised individuals from tampering with critical data.
Measures such as multi-factor authentication, biometric authentication, and strong password policies bolster security by verifying users’ identities effectively.
Furthermore, Johnson highlights the potential of blockchain technology for enhancing data integrity.
By leveraging cryptographic techniques and decentralised consensus mechanisms, blockchain creates an immutable and transparent ledger of transactions, making tampering virtually impossible without consensus from the network.
This distributed and decentralised nature ensures immediate detection and rejection of any attempts to tamper with data, thus preserving its integrity.
Moreover, Johnson emphasised the importance of data validation techniques such as checksums, digital signatures, and hash functions. These methods generate unique identifiers for data sets, allowing organisations to verify their integrity and authenticity.
Regular data backups and integrity checks complement these measures, enabling organisations to recover effectively from data corruption or loss incidents.
Johnson advocated a multi-faceted approach to ensuring data integrity, encompassing encryption, access controls, blockchain technology, data validation, and regular monitoring.
“By adopting these secure methods, organisations can fortify their defences against cybersecurity threats, preserving trust and confidence in their digital operations amidst an increasingly data-driven landscape,” she added.
WATCH TOP VIDEOS FROM NIGERIAN TRIBUNE TV
- Relationship Hangout: Public vs Private Proposals – Which Truly Wins in Love?
- “No” Is a Complete Sentence: Why You Should Stop Feeling Guilty
- Relationship Hangout: Friendship Talk 2025 – How to Be a Good Friend & Big Questions on Friendship
- Police Overpower Armed Robbers in Ibadan After Fierce Struggle